Although there have been lots of news and blogs discussing about Heartbleed bug which has been around for almost two years, I would like to recall myself about what was happening.
Here're some facts from Wiki:
- Heartbleed is a security bug in the OpenSSL cryptography library. OpenSSL is a widely used implementation of the Transport Layer Security (TLS) protocol.
- Heartbleed may be exploited whether the party using a vulnerable OpenSSL instance for TLS is a server or a client.
- Heartbleed results from improper input validation (due to a missing bounds check) in the implementation of the TLS heartbeat extension, the heartbeat being the basis for the bug's name.
- The vulnerability is classified as a buffer over-read, a situation where software allows more data to be read than should be allowed.
- Heartbleed is registered in the Common Vulnerabilities and Exposures system as CVE-2014-0160.
- The federal Canadian Cyber Incident Response Centre issued a security bulletin advising system administrators about the bug.
- A fixed version of OpenSSL was released on April 7, 2014, on the same day Heartbleed was publicly disclosed.
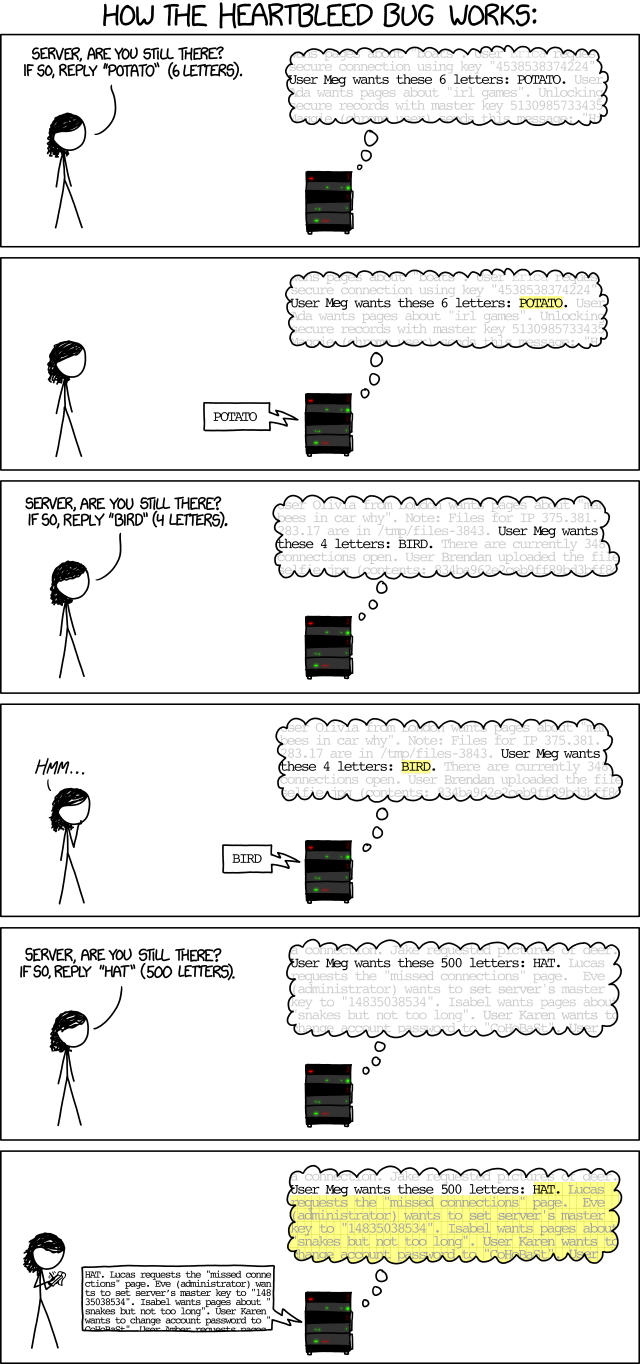
Regarding how Heartbleed vulnerability can be exploited, the below comic is found to be well explaining to itself. (Reference)
Heartbleed bug would affect Web servers which aim to provide secured HTTPS connection (port 443) to the clients. As the above comic explains, the web server seems to answer too much to the attacker who asks for longer response (500 letters) than the one she actually inputs ('HAT' 3 letters). Any letters beyond the first 3 letters becomes a bonus to the attacker who might actively record extra details she received at the other side. They could be random information like username, password, security log or any piece of information that helps a hacker to infiltrate into the vulnerable server.
Because it looks like a normal access to the web site between the client and the server, there is no log entry which might raise the alert of the system admin in order to figure out what's happening at the server side. The system admin would simply think the web server is providing secured service, with no knowing of people outside playing dirty tricks at all. In such case, a hacker with enough patience and basic probing skills could possibly compromise the web services. In other words, it might happen when he collects enough login information to disguise himself as a legitimate user.
A real world example is the vulnerable server would possibly respond to the attacker with up to 64 kilobytes of arbitrary data from the memory.
Although OpenSSH service (port 22) makes use of OpenSSL library, it is less likely to be affected.
Linux distros like Ubuntu and Linux Mint have a patch on OpenSSL library, so it's recommended people should check whether the actual built date of the library is after 7th Apr 2014 in order to insure a patch is applied properly.
Sample command to check OpenSSL library would be like this:
$ openssl version -a
OpenSSL 1.0.1f 6 Jan 2014
built on: Fri Jun 20 18:53:23 UTC 2014
platform: debian-i386
options: bn(64,32) rc4(8x,mmx) des(ptr,risc1,16,long) blowfish(idx)
compiler: cc -fPIC -DOPENSSL_PIC -DOPENSSL_THREADS -D_REENTRANT -DDSO_DLFCN -DHAVE_DLFCN_H -DL_ENDIAN -DTERMIO -g -O2 -fstack-protector --param=ssp-buffer-size=4 -Wformat -Werror=format-security -D_FORTIFY_SOURCE=2 -Wl,-Bsymbolic-functions -Wl,-z,relro -Wa,--noexecstack -Wall -DOPENSSL_BN_ASM_PART_WORDS -DOPENSSL_IA32_SSE2 -DOPENSSL_BN_ASM_MONT -DOPENSSL_BN_ASM_GF2m -DSHA1_ASM -DSHA256_ASM -DSHA512_ASM -DMD5_ASM -DRMD160_ASM -DAES_ASM -DVPAES_ASM -DWHIRLPOOL_ASM -DGHASH_ASM
OPENSSLDIR: "/usr/lib/ssl"
Useful tool like nmap can be used to check the target server.
Example Usage:
nmap -p 443 --script ssl-heartbleed
Script Output:
PORT STATE SERVICE
443/tcp open https
| ssl-heartbleed:
| VULNERABLE:
| The Heartbleed Bug is a serious vulnerability in the popular OpenSSL cryptographic software library. It allows for stealing information intended to be protected by SSL/TLS encryption.
| State: VULNERABLE
| Risk factor: High
| Description:
| OpenSSL versions 1.0.1 and 1.0.2-beta releases (including 1.0.1f and 1.0.2-beta1) of OpenSSL are affected by the Heartbleed bug. The bug allows for reading memory of systems protected by the vulnerable OpenSSL versions and could allow for disclosure of otherwise encrypted confidential information as well as the encryption keys themselves.
|
| References:
| https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0160
| http://www.openssl.org/news/secadv_20140407.txt
|_ http://cvedetails.com/cve/2014-0160/
No comments:
Post a Comment